Fortifying Your Industrial Network: 5 Essential Tips for Unwavering Security
In today’s interconnected world, industrial networks are the backbone of critical infrastructure and manufacturing processes. These networks play a pivotal role in ensuring the smooth operation of power plants, factories, water treatment facilities, and more. However, their importance also makes them prime targets for cyberattacks. With the increasing frequency and sophistication of cyber threats, it’s imperative to fortify your industrial network to ensure unwavering security. In this article, we’ll explore five essential tips to help you bolster your industrial network’s defenses.
Conduct a Comprehensive Risk Assessment
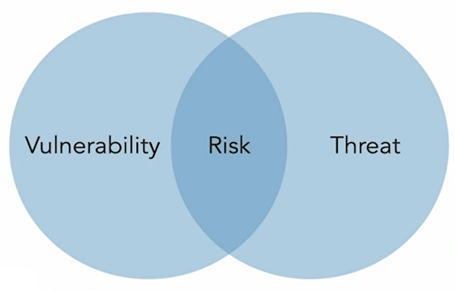
The first step in securing your industrial network is to understand the risks it faces. Conducting a thorough risk assessment is crucial to identify potential vulnerabilities and threats. Engage with cybersecurity experts who specialize in industrial systems to assess your network’s current security posture. This assessment should encompass:
Identifying Critical Assets: Determine which components of your industrial network are most crucial for operations and prioritize their protection.
Vulnerability Assessment: Identify potential weaknesses in your network’s hardware, software, and configurations.
Threat Modeling: Evaluate the types of cyber threats that could target your network, including malware, insider threats, and external attacks.
Regulatory Compliance: Ensure that your network adheres to industry-specific cybersecurity regulations and standards, such as NIST’s Cybersecurity Framework or the IEC 62443 series for industrial control systems.
Implement Network Segmentation
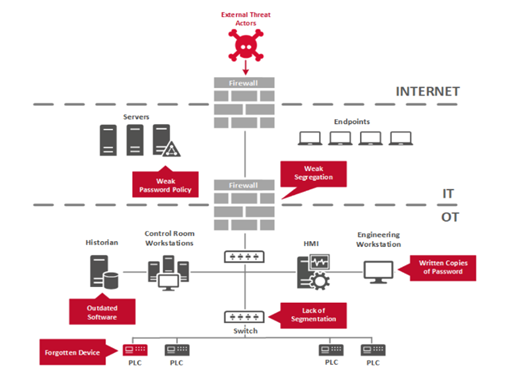
Network segmentation involves dividing your industrial network into smaller, isolated segments. This limits lateral movement for attackers, making it harder for them to compromise critical systems. Segmentation can be achieved through physical or virtual means and should consider factors like data flow, functionality, and security requirements. Implementing proper segmentation can:
Minimize the Attack Surface: By isolating critical assets, you reduce the potential entry points for attackers.
Enhance Control and Monitoring: Each network segment can have its own security policies and monitoring, allowing for more granular control.
Simplify Compliance: Isolating sensitive systems can make it easier to demonstrate compliance with regulatory requirements.
Deploy Robust Access Control Mechanisms

Access control is the cornerstone of network security. Implement strong authentication and authorization mechanisms to ensure that only authorized personnel can access your industrial network. Here are some best practices:
Multi-Factor Authentication (MFA): Require multiple forms of verification, such as a password and a token or biometric data, to access critical systems.
Role-Based Access Control (RBAC): Assign access privileges based on job roles to limit user access to only what’s necessary for their tasks.
Regularly Review and Update Access Permissions: Periodically review and revoke access for employees who no longer need it and ensure that access rights are aligned with job responsibilities.
Continuous Monitoring and Intrusion Detection

Real-time monitoring and intrusion detection systems are essential for identifying and responding to security threats promptly. Invest in tools and technologies that can:
Monitor Network Traffic: Analyze network traffic patterns to detect anomalies or suspicious activities.
Log Management: Keep detailed logs of network activities and user actions to aid in forensic analysis.
Intrusion Detection and Prevention systems (IDPS): Employ IDPS to detect and block known attack signatures and behavior patterns.
Security Information and Event Management (SIEM): Use SIEM solutions to aggregate and correlate data from various sources for a comprehensive view of your network’s security posture.
Regularly Update and Patch Systems
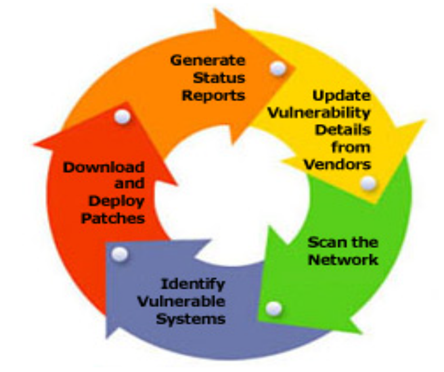
Cyber threats are constantly evolving, and attackers often target known vulnerabilities. Regularly update and patch all systems and software in your industrial network to stay one step ahead of potential threats. Here’s how to do it effectively:
Establish a Patch Management Process: Develop a systematic approach to identify, test, and deploy patches in a controlled manner.
Prioritize Critical Systems: Focus on patching critical assets first to mitigate high-risk vulnerabilities.
Test Patches in a Controlled Environment: Before deploying patches in your production environment, test them in a controlled, isolated environment to ensure they won’t disrupt operations.
In conclusion, securing your industrial network is not just a matter of technology but also a strategic approach to risk management. By conducting risk assessments, implementing network segmentation, enforcing access controls, continuously monitoring threats, and keeping software and firmware up to date, you can fortify your industrial network against a wide range of cyber threats. In an era where the convergence of information technology (IT) and operational technology (OT) is accelerating, industrial network security is a critical investment in the longevity and reliability of your operations. Stay vigilant, stay secure, and stay resilient in the face of evolving cyber threats.
We at Arist Middle East are well equipped with strong Industrial Cybersecurity knowledge and with specialized experience in Governance, Risk, Compliance (GRC) for OT environment. Please explore our website to learn more about our consulting services.
