Partnering with Trusted Vendors and Providers for OT Infrastructure
Operation Technology (OT) plays a pivotal role in critical infrastructure as well as enhancing productivity and optimization across various industries, from energy and utilities to manufacturing and transportation. Ensuring the reliability, security, and efficiency of OT infrastructure is of paramount importance. One of the essential ways to achieve this is by partnering with trusted vendors and providers.
Businesses rely heavily on supply chains to source products and services essential for their operations. While supply chains bring efficiency and cost savings, they also introduce cybersecurity risks that can have severe consequences for organizations. Neglecting supply chain management with trusted and reputable vendors can expose your business to a range of threats.
In this article, we will explore the significance of partnering with reliable, trustworthy vendors and providers for your ICS infrastructure and discuss the key factors to consider when selecting them. We will also explore the cybersecurity risks associated with not managing your supply chain effectively.
The Cybersecurity Risks
Counterfeit and Substandard Products:
When you source products from unverified or non-reputable vendors, you run the risk of receiving counterfeit or substandard goods. These products may contain vulnerabilities, hidden malware, or backdoors that can compromise your organization’s cybersecurity.
Data Breaches and Data Loss:
Untrusted suppliers may not have adequate security measures in place to protect the data they handle on your behalf. This can result in data breaches or data loss, potentially exposing sensitive information about your organization, employees, or customers.
Malware and Ransomware:
Cybercriminals often target the supply chain to introduce malware or ransomware into your organization’s network. Compromised software or hardware from untrustworthy vendors can serve as entry points for these malicious actors.
Weakened Infrastructure:
Poorly vetted suppliers may not adhere to industry standards for cybersecurity. This can lead to vulnerabilities in your infrastructure, making it easier for attackers to exploit weaknesses and gain access to critical systems.
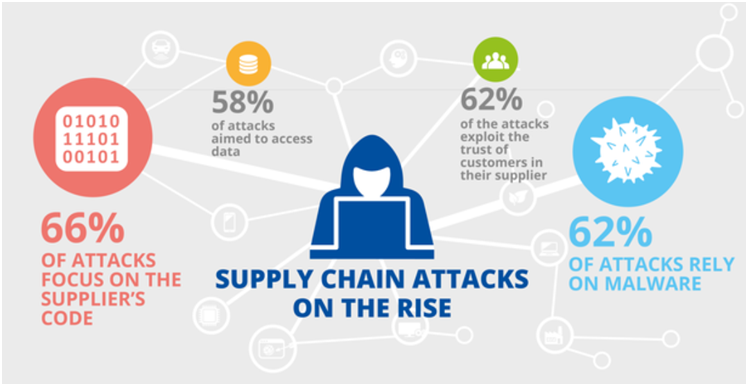
Supply Chain Attacks:
Supply chain attacks involve compromising a vendor’s systems to infiltrate your network. Unreliable vendors may have weaker security protocols, making them susceptible to these types of attacks, which can then extend to your organization.
Regulatory Non-Compliance:
Some industries are subject to strict cybersecurity regulations and compliance standards. Failing to vet your vendors for compliance can result in legal consequences and financial penalties for your organization.
The Importance of Trusted Partnerships in ICS Infrastructure

Enhanced Security:
A trusted vendor or provider is more likely to prioritize security in their products and services. They invest in robust cybersecurity measures to protect your ICS infrastructure from threats, vulnerabilities, and cyberattacks.
Quality Assurance:
Partnering with reputable vendors ensures that you receive high-quality products and services. This not only improves the efficiency of your ICS infrastructure but also minimizes the risk of downtime due to equipment failures.
Compliance and Standards:
Trusted partners are often well-versed in industry standards and compliance requirements. They can help you navigate complex regulations, ensuring that your ICS infrastructure remains compliant with relevant laws and guidelines.
Reliability and Support:
Reliable vendors and providers offer excellent customer support and maintenance services. In the event of issues or emergencies, you can count on their expertise to quickly resolve problems and minimize disruptions.
Security Assurance:
Reputable vendors invest in robust cybersecurity measures to protect their products and services. They are more likely to follow industry best practices and comply with security standards.
Risk Mitigation:
Trustworthy suppliers are proactive in identifying and addressing cybersecurity risks. They conduct regular security assessments and audits to ensure the integrity of their offerings.
Data Protection:
Reputable vendors understand the importance of data protection and privacy. They are more likely to have stringent data security measures in place to safeguard sensitive information.
Incident Response:
In the event of a security incident, trustworthy suppliers have well-defined incident response plans in place. They can collaborate with your organization to mitigate the impact of any breaches or attacks.
Long-Term Partnership:
Building relationships with trusted vendors fosters a sense of mutual trust and accountability. This can lead to better collaboration, shared security goals, and improved overall cybersecurity posture.
Key Factors to Consider When Selecting Trusted Vendors and Providers

Reputation:
Research potential vendors and providers thoroughly. Look for reviews, testimonials, and case studies to gauge their reputation within the industry. Speak with other businesses that have partnered with them to gain insights into their performance.
Experience:
Choose vendors and providers with a proven track record in the ICS field. Experience often translates to a deeper understanding of industry-specific challenges and the ability to provide effective solutions.
Security Measures:
Prioritize vendors and providers who prioritize security. Inquire about their cybersecurity protocols, encryption methods, and incident response plans. Ensure they are up-to-date with the latest security threats and best practices.
Product and Service Portfolio:
Assess the range of products and services offered. Ensure they align with your ICS infrastructure needs. A vendor or provider with a diverse portfolio can often provide integrated solutions that streamline operations.
Scalability:
Consider your future needs. Partner with vendors and providers who can scale their offerings as your ICS infrastructure grows or evolves. Scalability is essential to accommodate changing demands.
Customer Support:
Evaluate the quality of customer support and maintenance services provided. Prompt and efficient support is crucial in minimizing downtime and resolving issues swiftly.
Cost-effectiveness:
While cost should not be the sole determinant, it is essential to assess the overall value of the products and services offered. Consider the total cost of ownership, including upfront expenses, ongoing maintenance, and potential savings from improved efficiency.
Conclusion
The cybersecurity risks associated with neglecting supply chain management with trusted and reputable vendors are real and significant. In an era where cyber threats are constantly evolving, organizations must prioritize vendor vetting and due diligence as part of their risk management strategy. By partnering with suppliers that prioritize cybersecurity, you can reduce the likelihood of supply chain-related incidents, protect your critical assets, and maintain the trust of your customers and stakeholders.
Partnering with trusted vendors and providers for your ICS infrastructure is a strategic decision that can significantly impact the security, reliability, and performance of your critical systems. By carefully evaluating potential partners based on factors such as reputation, experience, security measures, and scalability, you can make informed choices that safeguard your organization’s critical assets and support long-term success.
Arista Middle East partnered with reputed and Trusted OT Cybersecurity solution providers and service providers which are best in class in the cybersecurity market today. This helps us to stand out and provide secure, reliable end-to-end solutions to our valuable customers. Please browse our website for more information. www.aristame.com
Top of Form
